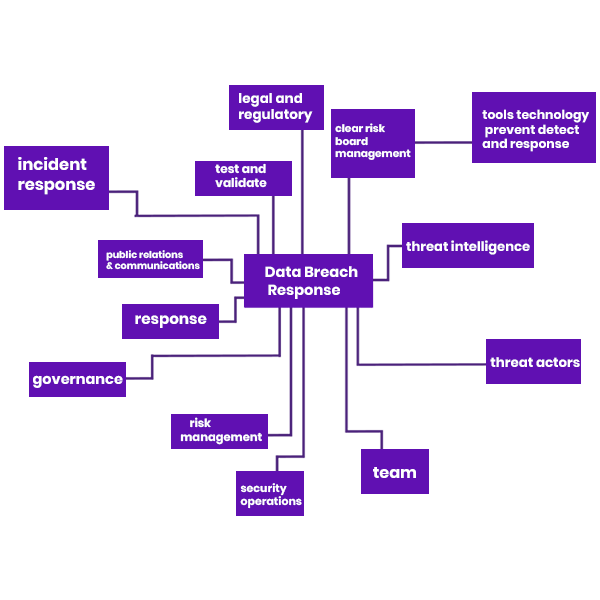
Security log monitoring and incident response

Agile Incident Response Plan
For Cybersecurity Strength
Our Proposal
Security breaches can occur without warning and go unnoticed for long periods of time. Security logs can help speed up and increase the efficiency of an incident investigation.
The ability of an organization to efficiently utilize all information at its disposal is critical to achieving efficiency in the field of incident response. Organizations execute security event logging and monitoring by checking electronic audit logs for indicators of unlawful security-related activity attempted or accomplished on a system or application that processes, transmits, or saves protected information. Security event logging and monitoring services assist clients in swiftly and cost-effectively weeding through system and audit logs, leaving only relevant records for analysis and retention.
Challenges
Our solutions
Disabled logging
As an information source that keeps track of important transactions with covered system, audit logs are also a prime target for attackers who are keen to hide their activities to maximize opportunities to compromise targeted data. Our log monitoring system may be set up to ingest both application and system logs, which are then processed in real-time.
Loss of trigger events due to overwritten logs
It is important to recognize that logs of operational events, while only incidentally involved in information security initiatives, may be of value to the organization. An audit of operational logs to identify any deviations from the compliance of security log management policy should prove helpful in proactively addressing any emerging issues. Retaining log data for at least 45 to 60 days and if you have the storage space, Infosec recommends extending this term to six months.
Failure to monitor logs
Infosec Future assists clients to manage information overload and focus on only the most important events that affect the confidentiality, integrity, and availability of their confidential data. We ensure all login, access control, and server-side input validation failures can be logged with sufficient user context to identify suspicious or malicious accounts and held for enough time to allow delayed forensic analysis.
Our Services:
Infosec Future strives to build a data security framework to keep your business and customer data secure with the following services:
Fast Alerts
We monitor all logs to set up alerts that notify of a specific problem with a system or application in real-time. Faster time to acknowledgment also means faster time to correction, implying that you've increased the overall quality and reliability of your application for clients.
Timely Analysis
With notifications sent in real-time, support or development employees can begin analyzing them as soon as possible. F aster acknowledgment of an issue means faster time to resolution. This serves to limit the end-user impact of a particular application or system.
Customized Plan
The ability to customize alerts ensures that the appropriate individuals are aware of application or system issues that they are competent to fix. We build a customized plan for each organization we work with.
IT Ticketing
When an event happens, our log monitoring solution automates the process of opening tickets. Automating such processes in the incident response process improves the overall efficiency of the strategy by speeding up the administrative components of incident response.