Incident Response and intelligence

Proactively respond to threats
Manage them like a pro.
Our Proposal
Infosec Future offers all of the necessary skills to provide data-driven businesses with configurable, consistent, and robust security log monitoring services.
For all organisations, our security logging, monitoring, and incident response solution addresses three major cycles of cybersecurity. From secure email logins to firewall upgrades, the InfoSec Future security log monitoring application keeps track of everything that happens in your environment. We keep track of all the occurrences that might jeopardize your IT ecosystem presently or in the future. We assist you in developing a response strategy to deal with any dangers that may come at any moment.
Challenges
Our solutions
Finding hard to Document the response plan
Our Incident response plans ensure that responses are as effective as possible. These plans are necessary to minimize damage caused by threats, including data loss, abuse of resources, and the loss of customer trust.
Monitoring strategy for any voluminous data
We won't be waiting for a security risk to arrive at your doorstep before putting together a protection plan. Our security log monitoring services start from the beginning and keep an eye on every data detail to keep your company running smoothly.
Standardizing log formats across all OS and devices
We provide a commercial solution for log collection, analysis, and reporting. Log management systems provide a configuration interface to manage log collection, as well as options for the storage of logs often allowing the administrator to configure log retention parameters by individual log source.
Our Services:
We provide you specialized services ranging from log monitoring and data maintenance to solutions and strategies for any future risks that may emerge.
24*7 Security Monitoring
We provide 24x7 security monitoring and incident response services to assist you to maintain a complex IT infrastructure. We never allow cyber threats to intimidate your firm because we address your whole IT infrastructure.
User and Administrative Activities
Our experts analyze your user and administrator activity to identify probable theft and compromise incidents. We search for things like login failures, time, location, characteristics, kinds, and SSO actions, among other things.
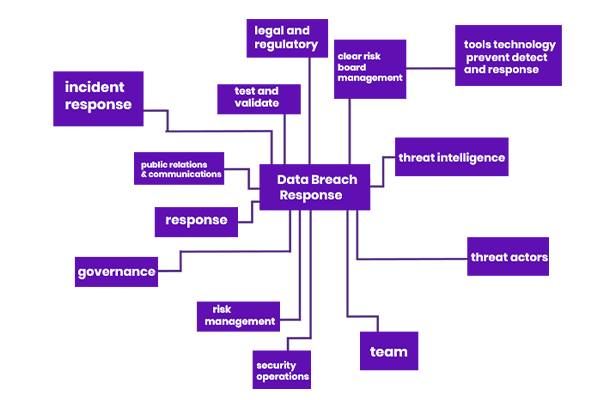
Incident Response plan
We've put together a complete guide to deal with any unexpected activities you could encounter, as well as a full-proof plan for dealing with them.